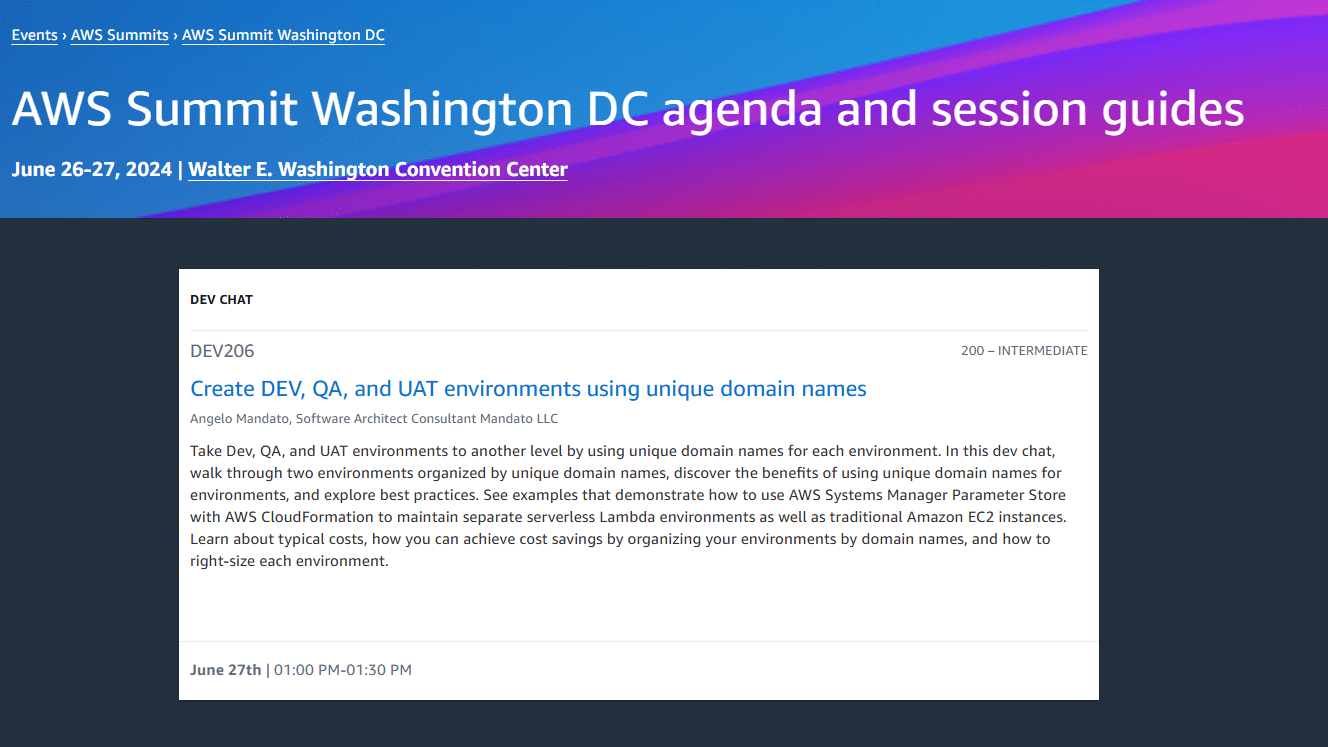
Presenting at the 2024 AWS Summit – Washington, DC
I am excited to announce I will be presenting at the 2024 AWS Summit Washington, DC. The AWS DC Summit

I am excited to announce I will be presenting at the 2024 AWS Summit Washington, DC. The AWS DC Summit

I am excited to announce I will be presenting at the 2023 AWS Summit Washington, DC. The AWS DC Summit

If you get the following error running PHP using the AWS SDK for PHP, then this post is for you!
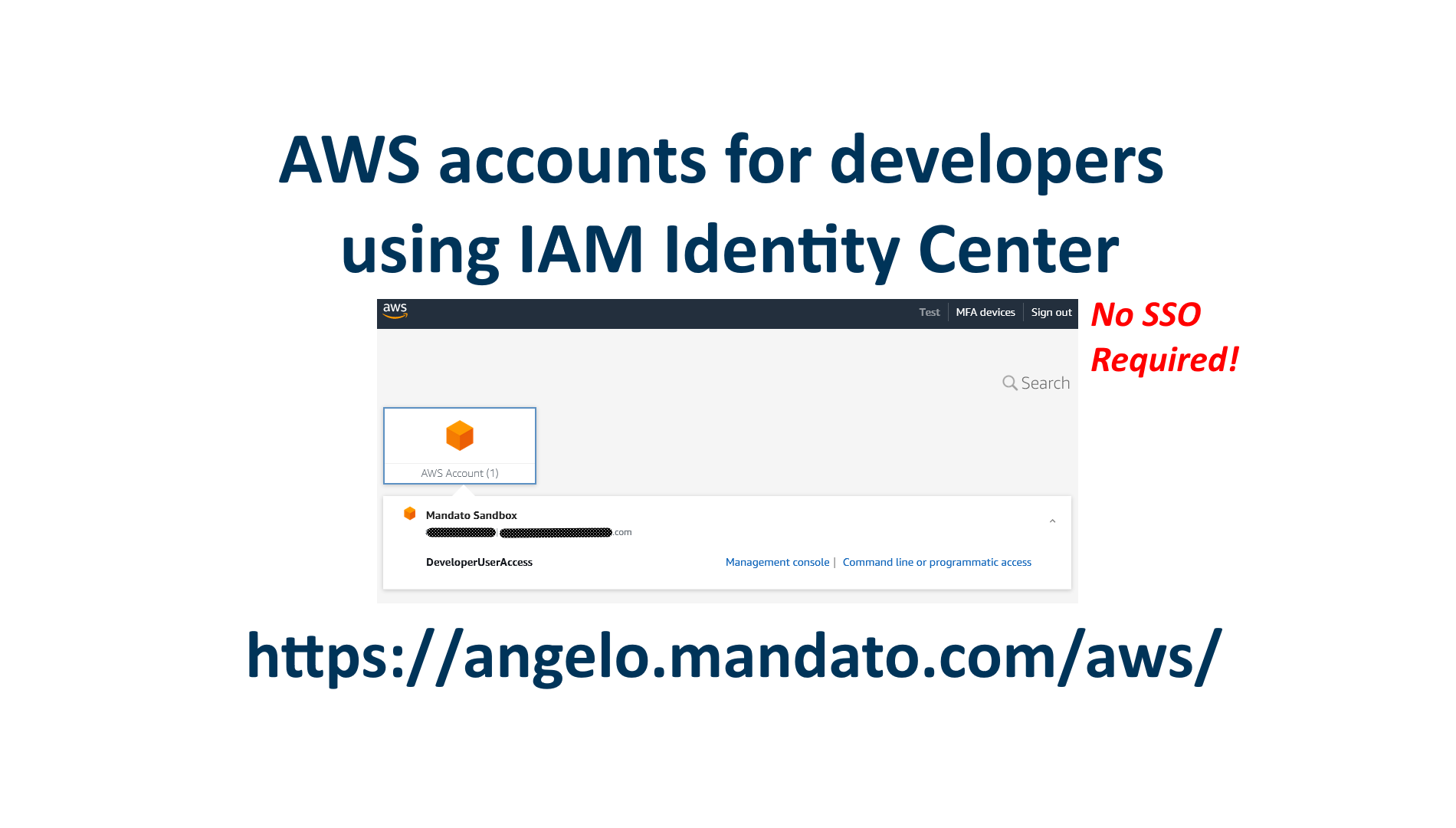
Learn how to easily setup IAM Identity Center to manage logins for developers to access AWS accounts for test and production environments. Developers can then sign in to the console or obtain temporary keys for programmatic access.

Files stored in AWS S3 can be redirected to specific URLs. By utilizing the S3 static website feature, a special

Redirect URLs with specific path prefixes or HTTP error codes on AWS using S3 static website JSON Redirection Rules feature.

Run API Gateway locally to develop and test before deploying into the AWS environment.
Redirect an entire website using Amazon Web Services maintenance free serverless resources.
Redirecting URLs on Amazon Web Services comes in a number of flavors depending on what you are trying to achieve
Changes you make today to improve your Google PageSpeed insights report will take 30 days to reflect in the FCP
If you are using Lets Encrypt (www.letsencrypt.org) certificates on your Ubuntu servers, you may find the following information useful if

If you have the error “Could not save password reset key to database.”, more than likely you have one of
Get the latest news and episodes of the Cloud Entrepreneur Podcast and Angelo’s development blog directly in your inbox!